Tailgate detection keeps critical areas safe
The HiveWatch® GSOC OS provides operators with something that access control alone can’t: the ability to confirm whether a tailgating incident has occurred. Tailgating, when one person badges through a restricted area and another person(s) follows through to gain access, can open up a business to potential threats.
Alert GSOC operators in real-time
Operators receive instant alerts in the event of a tailgating incident with the ability to confirm using video data

Tailgate detection keeps restricted areas from unauthorized individuals
In areas of high value or compliance, even the smallest opportunity for unauthorized access is unacceptable, which means a strong security countermeasure is required
Restricted areas require additional security protection protocols – especially when a posted guard is not feasible for the organization. Tailgate detection becomes a force multiplier for GSOC operators.
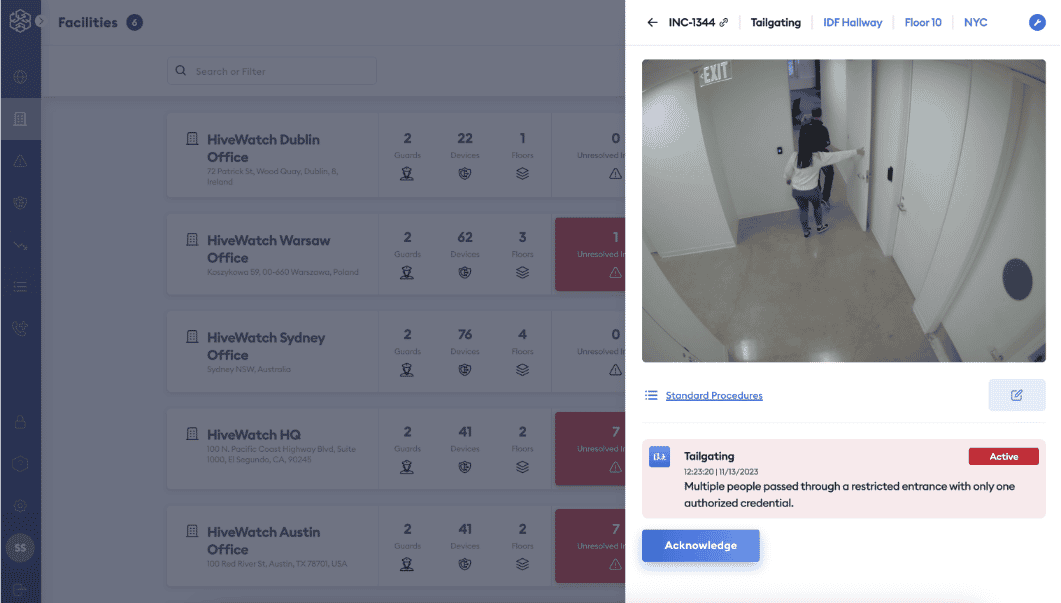
Automated detection saves valuable time and resources
Traditionally, tailgating has been approached by using turnstiles, anti-tailgating detection hardware (sensors), or badge programming like anti-passback, but each of these have their own disadvantages
The HiveWatch® GSOC OS provides a less obtrusive countermeasure with the ability to quickly identify the tailgating and dispatch a response, all while using existing video and access control technology
Built-in tailgate detection saves valuable time for an operator who would have to watch multiple feeds and entryways to manually detect tailgating incidents while they’re occurring

Additional Resources

Intelligent, Efficient, and Scalable Security for Large Venues
Event venues, arenas, and stadiums are turning to HiveWatch to increase the impact and efficiency of their existing security systems and programs, while offering a safer environment for patrons and employees.
The HiveWatch Difference
Want to know more about HiveWatch? Start here with an overview video featuring members of our leadership team. Discover the HiveWatch difference and the “why” behind our software.

Physical Security Needs a Makeover: How to Approach Security Differently
This eBook should speak to those who question how the siloed systems that your organization has invested in work together to provide more streamlined information to leadership, how technology needs to be open and able to ingest data being collected, and how fusion is the way forward.
